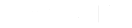Did you know 53% of people rely on memory to manage their passwords?
Simple passwords are easy to remember, but also easy to guess, leaving your data wide open to cyber-criminals. Password management is the solution.
Think about it. Whether it’s for your online shopping account or your social media, what kind of password do you usually pick? A strong combination of letters, numbers and symbols or a simple password that you can easily remember? With many people, it’s usually the latter. We’ve been told that writing passwords down is a cardinal sin when it comes to data security, so having a password that is easy to remember is a good thing, isn’t it? Unfortunately not. Simple passwords make life easy for hackers who are looking to gain access to your data. Furthermore, if you use the same passwords for multiple accounts, you’re providing access to all of those accounts to the hacker who successfully infiltrates your password.
What implications does this have on business data? Employees who don’t have to abide by a password management policy are likely to choose easy passwords and use the same passwords for business accounts as they would for their personal accounts. Complicated passwords are great for keeping hackers out of your accounts and safeguarding your data, but they are difficult to remember, especially if you have a variety of passwords for different accounts. The answer to this issue is password management. So let’s jump into what password management is and how it will improve your team’s password etiquette without them having to memorise a list of complex passwords.
What is Password Management?
In the digital era, there are many threats when it comes to password management. From login spoofing, where criminals create fake login pages to collect credentials to using tools, such as key loggers to steal passwords, there are many opportunities for attackers to gain unauthorised access to accounts. Like all methods of cyber-attacks, password theft is becoming more advanced, yet businesses are still relying on traditional methods of password management, such as writing passwords down, using simple passwords, relying on the ‘forgotten password’ option instead of keeping records and not implementing rules for creating and managing passwords. In general, good password management involves a set of policies, best practices and tools that are used together to ensure that users are storing and managing passwords safely. So, now we know what it is, let’s explore how you can implement effective password management into your business.
Creating a Password Management Policy
A good password management policy outlines the rules you want to implement for password administration and management, as well as explaining what a user needs to do in the event of a security issue. In terms of how in-depth your password management policy should be, that’s up to you. It can be a few simple rules or a detailed breakdown of protocols and instructions. At a basic level your policy should outline:
- What constitutes a strong password, e.g. avoiding identifiers, such as names and birthdays, choosing a random combination of upper and lowercase letters, numbers and symbols.
- Rules regarding password resetting.
- How often users should change their password.
- Misused passwords procedure.
- What to do in the event of a security breach.
Ensure this policy is circulated to your current team, introduced during a new employee’s induction and so everybody knows exactly what is expected of them when it comes to password management. Also, ensure your team knows who to reach out to should disaster strike.
What is Password Management Software?
Using password management software (AKA a password manager) enables you to create high-strength passwords that are stored securely within the software. The intuitive manager then auto-fills the relevant password into applications and websites, thus solving the dilemma of using complex passwords without having to remember them or write them down. Every password-protected application and programme can have its own password therefore eradicating the mistake of using the same password for multiple accounts. There are different types of password managers, including applications for PCs and mobile devices, as well as browser extensions, so which one you choose to use depends on your needs.
Now, you may be wondering, a password manager is an application – can’t applications be hacked? If so, why would I want to store all of my passwords in a bank that can be hacked into and provide access to all of my accounts to a criminal? As long as you choose a password manager from a trusted, established provider the risks are minimal. Reliable password managers created by reputable providers include secure encryption and layers of added protection to keep your passwords safe. Furthermore, users will usually have to go through an additional barrier, such as multifactor authentication in order to access their passwords anyway. With a password management software, your passwords are under lock and key and can be securely used whenever you need.
Keep Your Data Under Lock and Key with Netcentrix
Whether you’re looking for advice on password management, implementing an effective password policy or are wondering which password management tools are right for your business, the experts at Netcentrix can help. Our specialist team can help you with all aspects of data security from implementing secure home working to safeguarding your premises with perimeter security and utilising multifactor authentication to keep your data secure.