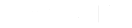What Security Controls Does a Business Need to Defend Itself Properly?

According to data from the 2024 Cyber Breaches Survey by the UK Government, 50% of all businesses in the country suffered a cyber attack or breach during the 2023/2024 winter period. A closer inspection reveals some interesting key insights, though. It appears the size of the business is a deciding factor in whether or not cyber criminals choose to launch an assault with 70% of medium businesses and 74% of large businesses coming under attack. Many charities are also targeted, with those with an annual income of half a million pounds or more remaining close to the top of criminals’ to-do list (66%) and hence managed it support for charities has never been so important.
These statistics reinforce the need for robust and reliable cyber security and risk management for businesses of all sizes and areas of speciality, if they wish to avoid the pitfalls of a successful attack or breach, which can be catastrophic. Disruption is the obvious risk in this scenario, but businesses can also suffer severe financial losses, irreparable reputational damage, and even legal troubles and permanent closure if the business in question fails to uphold all relevant regulations in protecting customer data.
Thankfully, advancements in technology throughout the years have also given rise to more advanced cyber security and cloud security tools and protocols that can boost an organisation’s security posture, helping maintain business continuity and avoid potential disaster on all fronts. But what precise tools and methods can your business use to keep itself safe in the face of evolving threats? Continue reading to learn more about how cybersecurity works and how you can use it to raise your operational security.
Cyber Security Measures You Can Take To Protect Your Business
Cyber Security Audit
Before we get into specific tools and methodologies, if you’re concerned your business has fallen behind the times on the cyber security front, there are ways you can solve such worries quickly and efficiently. Without the need to spend countless hours investigating multiple security tools that could, or could not, be of use. A full cyber security audit by a trusted and experienced cyber security company can offer you an all-encompassing solution to your cyber security concerns and tell you precisely where improvements need to be made, with penetration testing and specific advice on the tools and protocols you should follow to benefit the most.
Indeed, you may already have in-house IT staff whose role entails managing your organisation’s existing security policies. However, with familiarity comes the possibility of complacency, and it may be the case that your in-house staff simply miss important elements of your cyber security that need to be updated or are not as familiar as they should be with the most up-to-date advancements. So, even if you have staff on-site to deal with cyber security issues, it can always help to reach out for a second set of eyes, especially if you’re constantly dealing with attacks or have already suffered a serious breach. At Netcentrix, we don’t look at your business as one out of many; we take the time to get to know your business with a thorough audit and assessment which also takes into account your ways of working. That way, we can offer you the tools and services we know you’ll benefit from the most in the shortest amount of time, without needlessly spending on new tools you don’t need. With decades of combined experience in the cyber security and business technology space, our cyber security audit service will give you a comprehensive overview of your security strengths and weaknesses, so you have a crystal-clear view of where improvements need to be made. Then, we can put together a package of cyber security solutions that will serve your needs, giving you the peace of mind you need to continue running your business and serving your customers effectively.
Education
While technology will be an important defence for your business, it is also essential to offer your staff the knowledge they need to help prevent cyber security breaches and to spot more ‘personalised’ attacks that trick so many people. Phishing, for example, proved to be the number-one weapon of choice for cybercriminals attempting to breach systems, according to the Cyber Breaches Survey mentioned above, with 84% of attempted attacks being of this type.
If you’re unfamiliar with it, phishing is the process in which cyber criminals attempt to fool someone into offering sensitive information, like usernames, passwords, and even credit card information, in the guise of legitimate communication. These phishing attempts may also ask someone to access a website or click a malicious link which, in turn, often installs deadly malware without the user knowing.
These links usually come in the form of an email which has been designed to look like genuine communications from an organisation and can even take the form of an internal communication, making it easy for employees to click a dangerous link thinking they’re acting in the best interests of the company. Beyond stern email security (more on that in a moment) and good instincts on the part of the employee, these threats can be hard to repel and even harder to identify in the first place, especially if they’re well-made. This is why regular education and cyber security training is so helpful.
By keeping all employees aware of common and emerging cyber threats like the ones mentioned above, businesses are giving their staff the best chance at spotting such attempted attacks early, before they make a mistake and put sensitive data or their systems at risk. Given that the vast majority of data breaches are caused by human error, in a similar fashion to the above scenarios, this type of training should be considered absolutely essential. Again, working with an experienced and reliable cyber security expert to offer staff such training can make the difference between businesses maintaining ironclad security in the face of intelligent cyber criminals, or suffering a potentially business-ending attack.
Updated Cyber Security Tools
Now that we’ve discussed how people can give their businesses the best shot at keeping cyber attacks at bay, let’s take a look at how different types of security technology can offer a similarly beneficial line of defence.
Firewalls
One of the most widely-used pieces of network security since its inception, firewalls are a must-have tool for businesses seeking to protect their internal networks from unwanted traffic. A good way to think of a firewall if you’re not familiar with it is to imagine an actual, physical firewall. This is where the term ‘firewall’ in a cyber security context comes from. During a building’s construction, walls will be erected with the precise intention of stopping a fire from spreading should one start unexpectedly, to prevent further damage to the property or adjacent properties.
Just as physical firewalls prevent the passage of fire between one area and another, cyber security firewalls prevent the passage of unwanted network traffic between wider networks (such as the internet) and your internal business network. This is to prevent damage being caused by such traffic that may carry dangerous contents, such as malware.
Modern firewalls mostly inspect and prevent the passage of traffic based on three factors: state, port and protocol. User-defined protocols can also be implemented to ensure only desirable traffic is allowed to access your business network, based on pre-determined factors. However, next-generation firewalls (NGFW) take this process a step further and perform ‘deep’ inspections of packets (the pieces that contain the traffic attempting to access a network) comparing the contents of these packets to previously identified network dangers, so it can block them promptly, even if they’re well-hidden. These modern firewalls can exist as part of an on-site security system or can be hosted within the cloud.
Antivirus Software
While a firewall is a fantastic tool built to block potentially harmful network traffic from accessing your business network, antivirus programs are an example of endpoint security that’s designed to protect your individual machines, such as laptops, desktops and smartphones. Antivirus software scans all the elements of the machine in question, including new and upcoming pieces of data, to block harmful software from being installed and causing damage. This software can also be utilised as part of your mobile security on mobile devices. If a business machine unexpectedly downloads malware, the attack could perform several actions that will result in downtime and losses. These include, but aren’t limited to:
- Encrypting the data stored on the device – making it unreadable and holding it for ransom.
- Stealing data – so cyber criminals can use it for nefarious purposes, such as identity theft.
- Or destroying the system entirely – such malware can completely eliminate the operating system, rendering the machine useless.
Another common form of malware is spyware, in which a piece of malicious software is unknowingly installed on a device, allowing the creator to monitor all activity on the device at all times. This gives the creator access to all sensitive information shared on the device, including usernames and passwords, which can be gathered through key tracking.
Modern, up-to-date antivirus software helps to fend off attacks from all of the above and more, making it a necessity for all business devices.
Autonomous Network Monitoring
A more recent innovation in data security than some of the other tools mentioned above, businesses now have access to tools that can autonomously monitor network security and activity, utilising advancements in artificial intelligence and machine learning, that can detect and destroy potential threats before they’ve even had the chance to launch an attack on a business network. These tools are particularly useful as they require no input from the part of the user and are often hosted by a third-party provider off-site via the cloud, taking pressure away from in-house staff and devices.
Multi-Factor Authentication
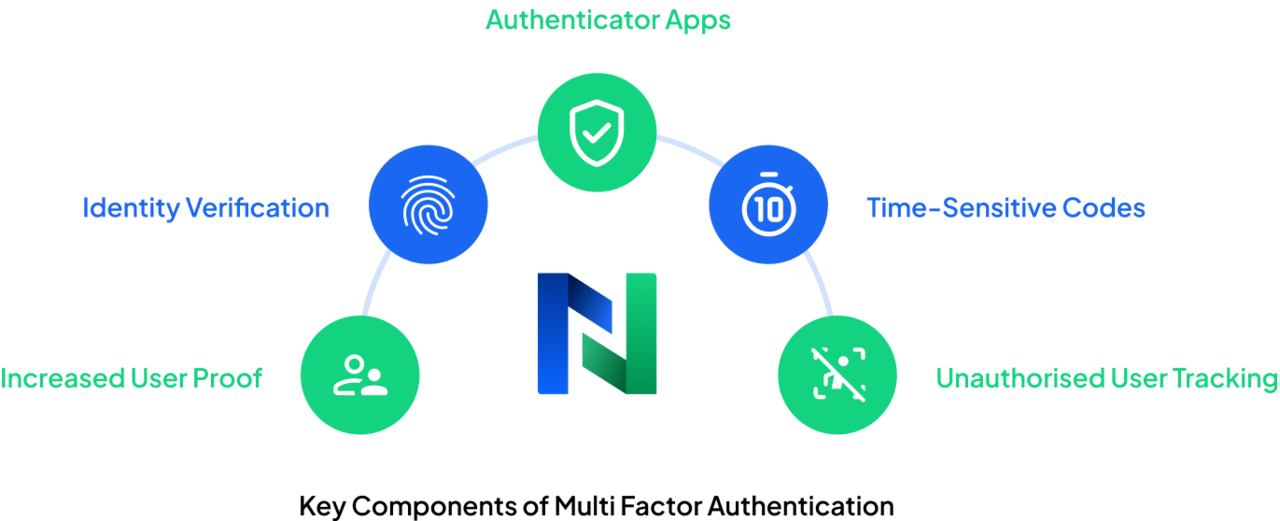
Logging into and out of business devices, programs and cloud environments time and again can feel like a chore, but it’s an essential practice that’s in place to prevent unauthorized access attempts and the dire consequences that could come about as a result. However, with so many of these devices, programs and environments now being accessed remotely by anyone with the correct details, extra security measures need to be put in place to guarantee only authorised users can access such materials, even if they have the correct login information.
Multi-factor authentication has become commonplace for countless consumer devices, applications and accounts, such as email accounts and online banking portals. It demands a user prove they are who they say they are by confirming their identity on a separate device or account, such as a smartphone or alternate email address, before being granted access. Authenticator apps are also common, which produce time-sensitive codes users can enter to gain access to an account. As these codes are constantly changing, it makes it exceptionally harder for cyber criminals to not only gain access to such a code, but to use it in time to access a device or account unlawfully.
Most users these days are competent enough to use multi-factor authentication on an individual level. But, when it comes to protecting all company accounts and devices, businesses need strategic and streamlined multi-factor processes in place to ensure ultimate safekeeping. Because of this, subscribing to a multi-factor authentication solution for businesses is a wise move. This allows company-wide authentication processes that are approved by IT and security managers, while also offering the relevant parties notifications in the event someone is unethically trying to gain access to a device or account, so they can be dealt with accordingly.
Give Your Business the World-Class Security it Needs with Netcentrix
While all of the above are excellent examples of how cyber security tools and protocols can be used to protect your business data, they’re barely scratching the surface of the in-depth services we offer at Netcentrix. With industry-standard accreditations across our entire team, as well as a wealth of previous experience, we’re your first choice for cyber security essentials for business and can help your company uphold consistently high security standards, for the benefit of both your business and your customers.
With Netcentrix, you’ll be assigned a dedicated account manager who will oversee the decision-making and implementation regarding your new cyber security additions, ensuring all tools meet your needs precisely and will serve you well now and in the future. Plus, should you ever encounter any technical issues with your new tools, our world-class support team is only a message away.To find out more about cyber security from Netcentrix, speak to a Netcentrix expert today.
Fill out our contact form and our specialists will get back to you soon!