- Perimeter security is a set of security measures designed to stop external threats from entering your network.
- Firewalls, Intrusion Protection and Detection Systems, and Virtual Private Networks (VPNs) are all examples of perimeter security used by businesses to protect their networks.
- Comprehensive perimeter security for businesses works best when onboarded through an experienced cyber security provider like Netcentrix.
Protecting Your Business Against Malicious Attacks with Perimeter Security
Perimeter Security cyber technologies provide a range of security services, from basic firewall protection to end-to-end security for your entire network and business. In essence, perimeter security is as it says, a defence system around your network designed to stop external threats from entering. Imagine your internal network as a castle; your perimeter network security consists of the weapons you’d put in place atop and around the castle (canons, archers, etc.) to defend from invaders – in this case, network threats.
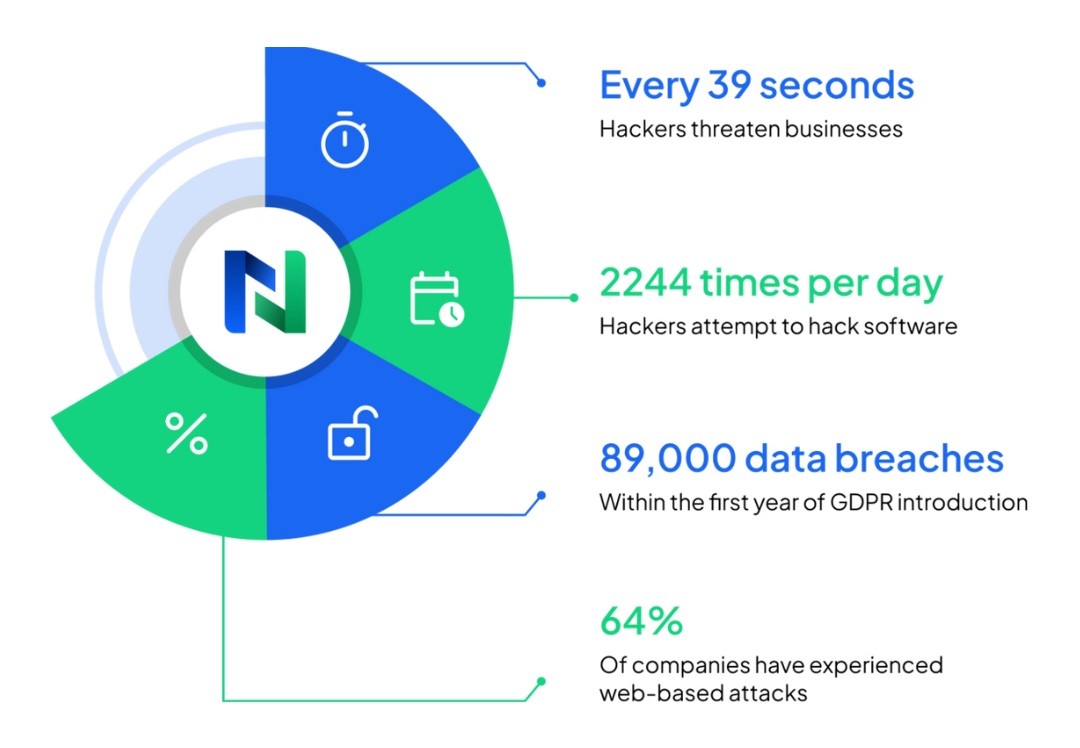
But why do we need cyber perimeter security systems for our networks? The statistics speak for themselves. Hackers attack every 39 seconds, on average 2,244 times a day. 43% of cyberattacks target small businesses while 64% of companies have experienced web-based attacks. 62% experienced phishing and social engineering attacks. 59% of companies experienced malicious code and botnets and 51% experienced denial of service attacks. In the GDPR’s first year, there were 144,000 complaints filed with various GDPR enforcement agencies and 89,000 data breaches recorded.
At Netcentrix, we are experts in network security and can offer bespoke services and guidance to help create a secure network perimeter and keep your systems clean. Read on to find out more about perimeter network security – and how we can help.
Why Do You Need Perimeter Security?
Short of unplugging your network from the rest of the world, cyber perimeter security is a necessary evil. Your best defence is to stop any breach before it gets past your main gates. In most cases, the simplest form of perimeter security is the boundary between your network and the internet. There are a number of layers to these defences starting with the initial entry point, your router.
Generally, your first physical line of defence is the gateway (your router) between your network and the big bad outside world (the internet). Routers serve as traffic signals for networks directing traffic in and out. Whilst your router will have some form of defence, it’s really only there to do a simple check on data entering and leaving your business – much like border control at the airport. It will do the initial check and either allow or deny data coming in and going out.
How Much Does Perimeter Network Security Cost?

The cost can be a factor when considering what kind of security your business deploys. However, according to WatchGuard, the global average cost of a cybersecurity attack reached a staggering $4.45 million in 2023. While this may be at the upper end of the scale and is more relatable to the largest of companies, its extreme nature emphasises the fact that cybersecurity should be seen as an investment, not an expense.
The Types of Cyber Perimeter Security and What They Do

Firewalls
Firewalls are the sniffer dogs in your security network, completing a much more thorough check for specific threats. Like airport security dogs, they have a set of rules and will either allow network traffic to pass or detect and deny specified threats. These guys pick up after your router and will complete a more thorough pass at filtering malicious traffic. Once traffic has made it past your firewall, there are still more layers which will look for suspicious data.
Intrusion Detection Systems
Intrusion Detection Systems (IDS) are the alarm system of your network security, detecting and warning you of suspicious activity, built from a single device or a series of sensors within your network at strategic points. Much like a police officer, an IDS will detect and report back to you that it may have found a suspicious character.
Intrusion Protection Systems
Intrusion Prevention Systems (IPS) are your army with shoot-to-kill orders. Compared to an IDS which just notifies you of a possible threat, your IPS will detect and attempt to automatically defend your data security system without your intervention.
As technology has advanced, some IPS have been combined with artificial intelligence (AI) tools that consistently scan network activity and shut down threats before they even have the chance to mount an assault, cutting the chances of you suffering a breach even further. What’s more, some modern systems also incorporate machine learning into their operation, looking for suspicious patterns in network activity and “remembering” this information so it can shut down threats even more acutely in the next instance.
Virtual Private Networks
Virtual Private Networks (commonly known as VPNs) reroute a device’s internet connection through an external provider, rather than using your own internet service provider. In the event your device comes under attack through your internet connection, the attack won’t be able to harm your device or your wider network because it will not be able to “locate” you. Instead, your connection will appear as though you are somewhere else entirely. This is why many consumers also opt to use VPNs to mask their physical location so they can take advantage of services not available in their home country. Think of VPNs as the invisibility cloak of the network security world, while leaving breadcrumbs for your pursuer to follow leading in the entirely wrong direction.
Choose Netcentrix for your Perimeter Security Needs

The most effective perimeter defence utilises multiple layers of complementary solutions, all of which work together to deny any potential intruder access to your network. When you choose a Cybersecurity solution from Netcentrix, you equip your business with a robust security solution which lowers operational costs and eliminates complex management. Our advanced multi-layered security solutions include threat management, intrusion prevention, web filtering and application control for the ultimate protection of your network.
With our impressive portfolio of firewall and Unified Threat Management services, we can equip your business with the right security solution, no matter your size or budget. From entry-level services to fully-featured perimeter security solutions, we can meet the most demanding threat protection requirements with our security solutions. Speak to a Netcentrix expert today.