Over 40% of businesses are seeking external advice on cyber security and cyber crime, according to the UK government’s 2024 cyber security breaches survey.
This is understandable, considering the same study revealed that over 50% of those businesses experienced a cyber attack in the previous twelve months.
Given the expanding and ever-evolving range of available options, it can be confusing to know which tools offer the security you need to protect critical data from cyber threats. However, by working with an experienced third-party security systems expert like Netcentrix, your business can arm itself with bespoke cyber security solutions designed to prevent cyber attacks while keeping data away from criminals. Ultimately reducing downtime and the spiralling consequences of a successful breach.
Learn more about our cyber security for business, or keep reading for more insight into useful security tools.
5 Cyber Security Tools and Protocols Your Business Could Benefit From
1. Firewalls and Anti-Virus
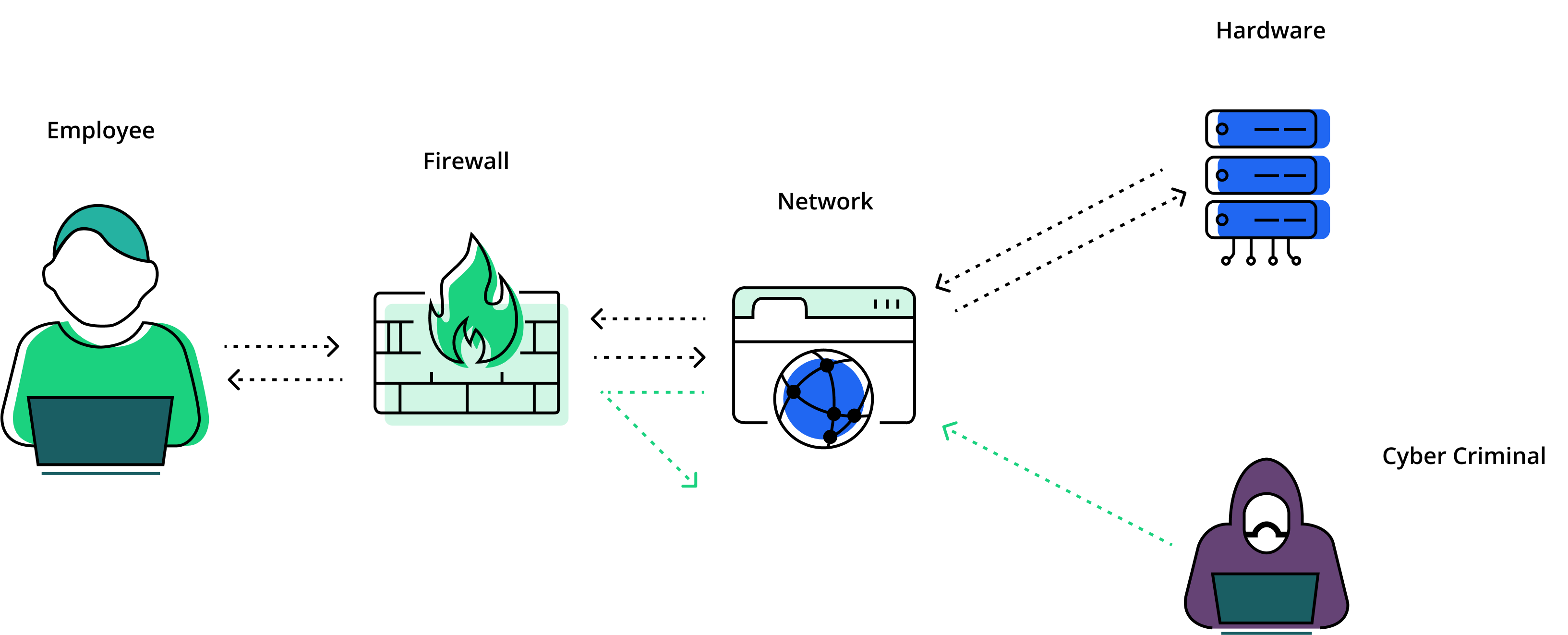
Firewalls and anti-virus programs have been staples in business cyber security for years and have evolved alongside the efforts of cyber criminals. A firewall is a tool that analyses incoming and outgoing traffic on a network, allowing safe traffic to pass while blocking harmful traffic from accessing network environments. The name “firewall” comes from the physical firewall, a wall designed to prevent the spread of fire in buildings.
These tools have always been useful, but modern firewalls have become even more advanced. By utilising AI (artificial intelligence) and machine learning, they can analyse data traffic, detect anomalies, and neutralise them using complex algorithms before threats have a chance to launch an attack.
Anti-virus programs operate in a similar way but focus more on protecting hardware and physical computer systems rather than network security. They scan devices and files for threats, alerting users to malicious downloads and preventing them from taking effect. Anti-virus software can also monitor websites and emails accessed by users, preventing hidden threats from being downloaded.

By utilising both anti-virus software and firewalls, businesses create a double-pronged approach to their defences, building a secure environment for both the network and business hardware.
2. Password Management
The days of using simple words and phrases as passwords are long gone. To keep data safe, it’s important to use longer, more complex passwords that are harder to decipher. Businesses should also use different passwords for each platform or account to prevent unauthorised access in case one password is cracked.

However, with numerous devices, platforms, and accounts in day-to-day use, it can be difficult to keep track of essential login information. Fortunately, password managers allow businesses to create and store intricate passwords on a secure server, making them easily accessible when new logins are needed.
While some may have reservations about storing sensitive login information with an external provider, password managers are generally regarded as a safe and efficient way to manage login credentials. They reduce the risk of forgetting or losing passwords, which could otherwise stall business operations. With approximately a third of internet users utilising password managers, according to Statista, the solution continues to be widely trusted.
3. Multi-Factor Authentication
A common component in modern account security, multi-factor authentication is used by millions worldwide to protect everything from social media to email accounts – and it’s equally valuable for enterprises.
Placing multi-factor authentication on essential platforms such as email accounts and communication systems is a simple step to deter criminals and prevent unlawful access, even if they have the correct usernames and passwords. Multi-factor authentication requires a user to confirm their identity on a separate device or account before access is granted, rendering any login attempts by a thief useless if they are trying to log in from a different location.

With 99.99% of accounts using multi-factor authentication successfully repelling unauthorised login attempts, according to data from Microsoft, it’s clear the process offers an exceptional level of protection.
At Netcentrix, we offer multi-factor authentication services for businesses seeking to add an extra layer of defence to their accounts and systems. Speak to a Netcentrix expert today to learn more.
4. Data Backups and Disaster Recovery
In the event of an on-site disaster, businesses that store all their data on internal servers and hard drives could find themselves in a precarious situation. Without effective data backup, business continuity is constantly at risk from various threats, including data breaches, natural disasters, fires, and more. Without the ability to restore data quickly, the likelihood of business disruption increases significantly.

This is why data backups and disaster recovery are essential components of modern cyber security. By backing up data off-site with a third-party provider like Netcentrix, businesses can restore everything from individual files to entire systems quickly via the cloud, without the need to wait for engineers or pay expensive repair costs.
5. Staff Training
While not strictly a “tool,” staff training can be an invaluable step in defending your business against cyber security risks. According to data from Stanford University, 88% of data breaches are caused by human error. This highlights the need for clear cyber security training to ensure employees handle data responsibly and maintain security standards.

Phishing is one of the most common cyber attacks in which employees unknowingly leak sensitive data. In a phishing attack, a cyber criminal contacts an employee, posing as a colleague or superior. They may instruct the employee to reveal sensitive login information or phone numbers, which could be used to bypass multi-factor authentication. The attacker may also try to convince the employee to click a link that downloads malicious software, spyware, or other threats.
While phishing is often done via email, it can also occur through instant messaging, WhatsApp, and other communication channels. By staying alert and applying the knowledge gained through comprehensive cyber security training, employees can better spot and report fraudulent messages and adopt proper security practices.
Choose Netcentrix to Upgrade Your Cyber Security and Defend Precious Business Data
If you’re concerned about security vulnerabilities and want to enhance your business’s defences against cyber criminals with modern, reliable solutions, speak to the team at Netcentrix. Our team have decades of combined experience in cyber security and are committed to staying at the forefront of industry developments through regular research and training. This allows us to offer you the most up-to-date solutions to protect your business and its data.
If you’d like to learn more about our cyber security services for businesses, get in touch with a Netcentrix expert today.