What if your business woke up to find sensitive customer data was leaked overnight?
According to Forbes, data breaches have surged by 72% from 2021 to 2023. This alarming increase highlights two main factors: cyber criminals are constantly evolving their tactics, and businesses may not be leveraging the most effective cybersecurity tools.

Whether caused by cybercriminals exploiting vulnerabilities or by human error, the reality is that both factors are contributing to this rise. For any business that wants to thrive in today’s digital landscape, preventing data breaches must be a priority.
But what exactly is a data breach? How devastating can they be to businesses, and what are the best ways to defend against them?
At Netcentrix, we’re experts in cyber security systems for businesses and have helped many enterprises tighten their security with modern, reliable cyber security tools.
Speak to a Netcentrix expert about preventing cyber security risks today, or keep reading to learn more.
Data Breach Definition
A data breach occurs when sensitive information is accessed, viewed, or stolen without authorisation.
Sadly, though, many criminals who unlawfully access a business’s network don’t stop there. They may also install malicious software, like spyware, or attempt to remove existing network security, further weakening the business.
While data breaches are often the result of cyber attacks in which criminals access computer systems and hard drives by hacking a network, account or device, this isn’t always the case. Around 9 out of 10 data breaches are caused by human error (more on this in a moment).
But however they occur, data breaches can have disastrous consequences for all – from small businesses to larger established enterprises – highlighting the need for effective, reliable cyber security across the board.
What are the Consequences of a Business Data Breach?
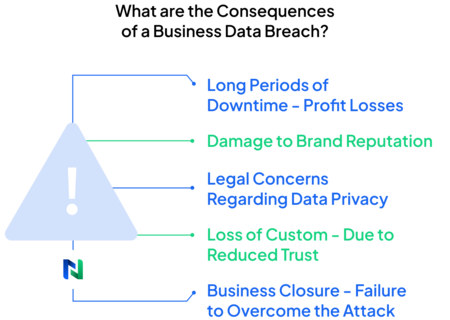
Here are just some of the consequences a business can expect to endure in the wake of a data breach or similar cyber crime:
- Significant Downtime
If critical data has been destroyed, businesses can spend elongated periods trying to restore or replace it, especially if they don’t have dedicated data backups.
With the cost of downtime rising into thousands, or millions in some cases, businesses cannot afford to be out of operation for too long.
- Reputational Damages
When businesses lose essential data, stalling operations, their reliability and trustworthiness are thrown into dispute.
As a result, customers and partners may choose to spend their money elsewhere.
- Legal Worries

When a data breach occurs, businesses must inform the relevant data protection bodies under whose rules they operate.
This isn’t just a helpful step to resolve the issue, it’s a legal requirement. Businesses must be able to prove they house and manage data responsibly at all times.
Failure to prove this could result in penalties, such as fines and closures.
- Loss of Custom
With customers having less and less patience as time goes on, they may switch to a rival business. This is due to the business failing to meet their needs promptly, as well as a lack of trust that may have developed as a result.
If elongated downtime is expected due to a data breach, businesses should anticipate clients and customers exploring other opportunities.
- Closure

It may sound like a worst-case scenario, but closure is a common side effect of suffering a data breach. In fact, 60% of small businesses close completely after a breach or successful cyber attack, according to data featured in Cybercrime Magazine.
Ways for Businesses to Prevent a Data Breach and Combat Cyber Threats
Working with a Cyber Security Expert

While in-house IT staff can help strengthen defences, they’re often not the in-depth solution a business needs.
For instance, these in-house workers may only be experienced in one aspect of data protection, while their knowledge of other essential areas is lacking.
But most businesses don’t want, or can’t afford, to pay multiple in-house IT technicians to offer the ironclad defences they’re looking for.
In these scenarios, it’s preferable to save money and work with third-party experts, like Netcentrix, rather than hiring more full-time staff.
With a team comprised of industry experts with a wide array of experience and knowledge, we can advise on the best bespoke cybersecurity tools and protocols to keep your data safe.
Ensuring All Security Tools are Up To Date
The older technology becomes, the more outdated it is – and the easier it is for criminals to manipulate.
This is why software companies work hard to offer constant updates and patches, keeping their creations working as effectively as possible while also strengthening defences against attacks.
The same can be said for cyber security tools, such as anti-virus programs, firewalls and VPNs. By keeping all these tools updated to the latest firmware, you’re limiting the ability of criminals to successfully make a breach.
Protecting Passwords

With numerous accounts, it can be difficult to create passwords that are intricate enough to not be broken, while also remembering them.
But predictable passwords, or passwords that have not been changed in a long time, are some of the easiest weaknesses criminals can take advantage of.
This is why it’s essential to use long, complex passwords (a mixture of upper and lower-case letters, numbers and symbols) to overcome the evolving tools used by hackers.
A password manager is a great way to keep track of things. Password managers are third-party solution providers that offer a secure, encrypted environment to store passwords and similar data, helping prevent the use of repetitive or easy-to-guess passwords.
Better still, some of these managers can help users create their own complex passwords, as well as change passwords when they’ve been in place for too long.
Multi-Factor Authentication
Another impressive tool thwarting cyber criminals in recent years, multi-factor authentication prevents unauthorised access to software and devices by requiring the user to confirm their identity on a separate device or account.
By placing multiple steps in a criminal’s way during attempted logins, the less likely they are to successfully log in to an account that does not belong to them, preventing data breaches.
Netcentrix provides multi-factor authentication solutions for businesses, to add an extra layer of protection to devices and accounts. Connect with a Netcentrix expert to find out more.

Employee Training
Because data breaches are so often caused by simple human error, with employees accidentally leaking sensitive data by sending it to the wrong person, employee data handling training is a great idea.
Such training could also help employees install security apps on their own devices, and avoid falling for tricks such as phishing – one of the most common cyber attacks.
Ideally, training should occur once every six months, or once a year at the very latest, and should include elements of data security employees may come across in their day-to-day, including:
- How to spot phishing emails
- How to report/dispose of suspicious emails and content
- Data handling protocols
- Password management
- Scanning devices for threats
- and more
By helping staff understand the correct processes involved in protecting data, not only is the likelihood of sensitive data being accessed by unauthorised parties significantly reduced, but it’s also encouraging proper compliance and responsible data handling – which could help avoid legal problems in the event of a breach.
Explore Cyber Security for Businesses and Fix Security Vulnerabilities with Netcentrix
If you’re concerned your business may be vulnerable to a data breach and that you’re not doing everything you can to protect sensitive company and customer data, reach out to Netcentrix.
Our team of experts will perform an analysis of your business systems and work with you to determine the best cyber security tools for your needs, so you can prevent data breaches and keep your operations moving, free of downtime.
When you partner with Netcentrix, you’ll be assigned a dedicated account manager who will ensure your new additions remain suitable for your needs, now and in the future.
Plus, with 24/7 technical support available if needed, you will always have access to the advice and knowledge you need.
To find out more about our cyber security solutions for business, speak with Netcentrix today.